On April 20, former acting CIA Director Michael Morell admitted he orchestrated the joint letter that torpedoed the New York Post’s bombshell reporting on Hunter Biden’s laptop in the weeks leading up to the November 2020 US Presidential election, at the direct request of Joe Biden’s campaign team.
That letter, published by Politico, asserted the leaked material bore unambiguous hallmarks of a Kremlin “information operation.” In all, 51 former senior intelligence officials endorsed the declaration on the basis their spying careers made them “deeply suspicious that the Russian government played a significant role in this case,” despite an avowed lack of evidence to support the charge.
This intervention was sufficient for Twitter to block all sharing of the NY Post’s exposés and ban the outlet’s official account. These measures were later undone due to intense backlash, but by then, the damage was done, and the articles thoroughly discredited. Joe Biden himself even cited the joint letter in a presidential debate with Donald Trump in order to deflect accusations of impropriety in his son’s Ukrainian dealings.
In private sworn testimony to the House Judiciary Committee, Morrell recounted how Antony Blinken, now secretary of state and then a senior Biden campaign official, reached out to him three days after the NY Post published an email indicating Hunter had introduced a Ukrainian business partner to his father.
Morrell, at the time tapped as a potential CIA director in a future Biden administration, avowedly organized the letter to “help [Biden]…because I wanted him to win the election.” Following Blinken’s call, he contacted retired CIA senior operations officer Marc Polymeropoulos for assistance in compiling the letter, and over the next two days gathered signatures from his intelligence community cohorts to lend an imprimatur of expert legitimacy to its dubious contents.
This revelation has reignited a welter of controversies, not least because the Elon Musk-approved “#TwitterFiles” recently exposed how the social network’s suppression of NY Post was executed despite significant internal doubts about the assorted intelligence officials’ “Russian disinformation” charge. Serious questions now hang over the Biden family’s activities in Ukraine, the legitimacy of the 2020 election result, and the role of Twitter and other social networks as effective wings of the US national security state.
28. To which former Deputy General Counsel Jim Baker again seems to advise staying the non-course, because “caution is warranted”: pic.twitter.com/tg4D0gLWI6
— Matt Taibbi (@mtaibbi) December 3, 2022
However, even critical voices have failed to acknowledge one of the most curious – and sinister – aspects of the joint letter psyop, which adds a whole other dimension to those burning concerns. There are strong grounds to believe that Twitter’s public suppression of the NY Post’s disclosures was complemented by a covert operation to identify and neutralize anyone discussing the contents of Hunter Biden’s laptop, courtesy of Dataminr, a social media spying tool heavily connected to British and American intelligence services.
As we shall see, Dataminr has previously been marketed to highly repressive foreign governments known for their criminalization of political activism and journalism, as a means of closely monitoring the activities of dissidents and scrupulously mapping the networks in which they operate, both on and offline.
If Dataminr was deployed in service of suppressing Hunter Biden’s emails, then its sweeping dragnet would’ve placed any Twitter user who discussed the leaked content, and all those who retweeted, ‘liked’, or commented on their posts, at risk of intensive monitoring censorship, suppression, and outright banning. All their associates could also then be placed under surveillance, and dealt with similarly if necessary.
In the offline realm, it could’ve placed all these individuals in the crosshairs of the FBI and DHS. Both maintain big-ticket contracts with the company.
Friends in high places
Among the signatories to the joint letter were a number of individuals tied to shadowy consultancy firm Beacon Global Strategies. Alongside Morrell himself, this included; Jeremy Bash, former CIA and Department of Defense chief of staff; Glenn Gerstell, former NSA general counsel; Rick Ledgett, former NSA deputy director; Leon Panetta, former CIA director and secretary of defense; and Michael Vickers, former CIA operations officer and under secretary of defense for intelligence.
Beacon’s barebones website offers few clues as to the company’s raison d’etre. It talks stultifyingly of “[developing] strategies that enable companies to achieve their business objectives,” and “[representing] global enterprises and industry disruptors across government services, technology, energy, and financial sectors.”
In practice, this amounts to securing customers for its clients from government, security, intelligence and law enforcement agencies the world over. Beacon’s 69-strong staff, almost exclusively comprised of Pentagon, CIA, NSA and State Department veterans, leverage their high-level contacts and access to generate lucrative state-level contracts.
Beacon’s client roster isn’t public, but it’s known to represent several startups funded by In-Q-Tel. As the CIA’s venture capital arm, it invests in an array of startups to ensure the US intelligence community maintains a “competitive edge” in all spheres of science and technology. A highly influential Silicon Valley trendsetter, for every dollar invested by In-Q-Tel in an emerging company, the private sector injects $18 on average.

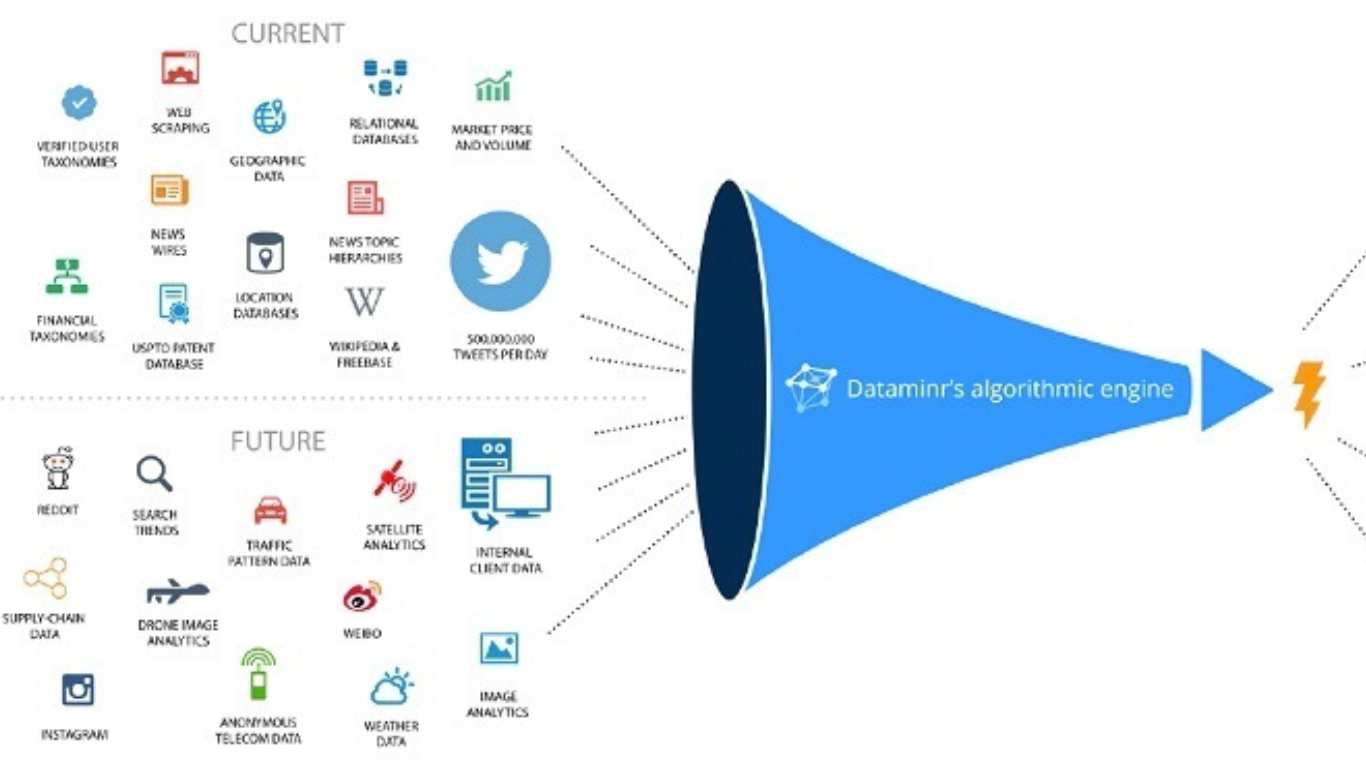
In 2016, The Intercept revealed In-Q-Tel was financing at least 38 separate social media spying tools, to surveil “erupting political movements, crises, epidemics, and disasters.” Among them was Dataminr, which enjoys privileged access to Twitter’s “firehose” – all tweets published in real time – in order to track and visualize trends as they happen.
Dataminr is the company with which Beacon Global Strategies is most publicly associated. Leaked documents and emails shed significant light on how business was drummed up for the firm at the highest levels, the world over.
In late March 2015, Philippe Reines, one of Beacon’s founders and its then-managing director, contacted Capricia Marshall, an old friend and colleague and ambassador in residence at the Atlantic Council, a NATO-funded ‘think tank’. As Mintpress News senior staff writer Alan Macleod has comprehensively exposed, the organization not only serves as the military alliance’s propaganda arm, has in recent years cemented a position policing the parameters of acceptable speech across social media platforms, through “counter-disinformation” partnerships.
Reines and Marshall had previously worked closely together under Hillary Clinton while she was the Obama administration’s secretary of state. Reines was one of her top aides, while Marshall was chief of protocol, a senior State Department liaison with foreign diplomats.
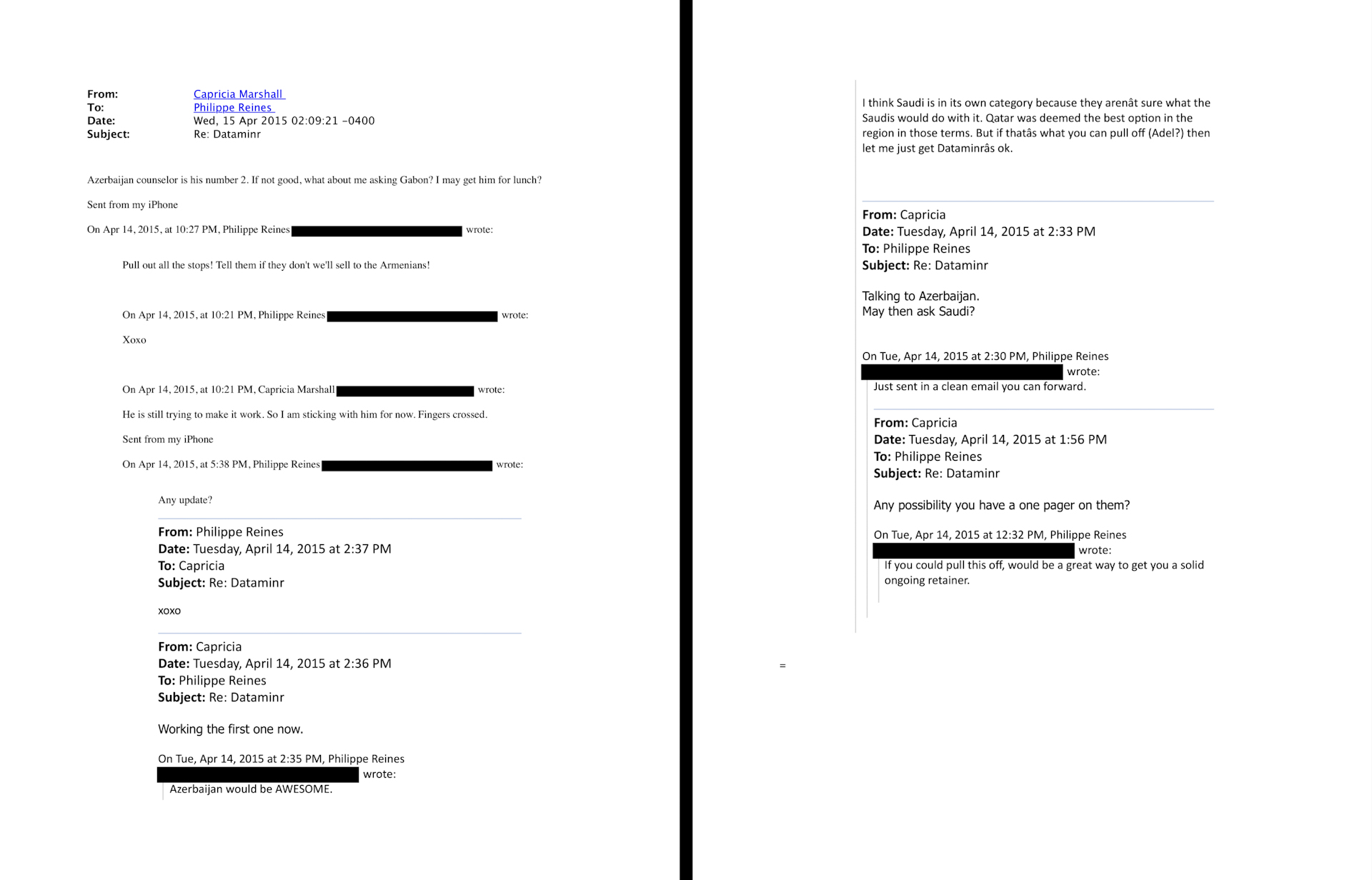
Reines wrote to Marshall that there was “one particular matter” he was working on “that’s right up your alley,” in reference to Dataminr. Marshall was highly amenable to his advances, and subsequent emails starkly underline why – Reines assured her that if she could successfully sell the company’s services to foreign governments, it would be “a great way” of securing “a solid ongoing retainer” from Beacon.
Marshall duly began extolling the virtues of Dataminr to foreign officials. Governments with appalling human rights records were of particular interest to Beacon, although there were limits to that appetite.
On April 14th, 2015, Marshall told Reines she was talking to the Azerbaijani government about Dataminr, and asked if Saudi Arabia would also be of interest. He responded that the country was “in its own category,” as Dataminr “aren’t sure what the Saudis would do with it.” Qatar was conversely “deemed the best option in the region.” He added that Azerbaijan “would be AWESOME [emphasis in original]” as a client.
In a subsequent email, with Marshall’s government contact in Baku apparently playing hardball, Reines implored her to “pull out all the stops!”, and “tell them if they don’t [buy] we’ll sell to the Armenians!”. Armenia and Azerbaijan have effectively been at war on and off since 1988. At time of writing, the latter’s blockade of Artsakh has entered its sixth month. All along, the breakaway republic’s 120,000-strong Armenian population has been deprived of basic essentials, including life saving medication.
Who watches the watchers?
Azerbaijan has since gaining independence from the Soviet Union in 1991 been notorious for its brutal repression of dissent, harassing, persecuting and imprisoning journalists and activists. In 2021, it was revealed Baku had invested in NSO Group’s Pegasus spying apparatus, and deployed it against critics at home and abroad.
A Dataminr presentation given to Azerbaijan’s US embassy at the time Reines and Marshall were back-and-forthing strongly suggests Baku may have had access to many of the same capabilities offered by Pegasus, in the context of social media, much earlier. A slide detailing a Dataminr service known as ‘Expanded User Detail’ shows how individuals on Twitter can very easily be identified and extensively monitored.
This resource swiftly locates the source of a popular tweet or breaking news alert, then their most popular tweets, what hashtags they have previously used, and who or what has shared their tweets, mapping the path of their posts. This includes an option for “geographic political analysis”, a euphemism for ideological affiliations.
If this resource was, say, employed against a protester whose footage of an anti-government demonstration in Baku went viral via Twitter, police, spies, and state officials in Azerbaijan could track down who they were, their political, personal and professional associations, and even potentially their family members at the click of a button.
Elsewhere in the pitch, Dataminr boasts how Twitter’s firehose means it produces public safety incident and terrorist attack alerts well in-advance of the media. An ‘About’ page towards the end highlights its “long-term strategic data and product partnership” with the social network, alongside its “partnership” In-Q-Tel.
By this point, Dataminr was thoroughly integrated with Western spying agencies. On June 15th 2015, Beacon managing director and White House intelligence veteran Michael Allen emailed Capricia Marshall, notifying her Dataminr representatives would soon head to London to meet with “all kinds” of government officials. Accordingly, he asked her to arrange a meeting at the British embassy in Washington in advance.
One week later, Marshall emailed British diplomat James Kariuki, stating it was “wonderful” to have seen again recently at the ambassador’s residence, and reminding him Beacon Global sought to connect with him “on a few issues.” “In particular,” she wrote, “a client they are introducing to people at 10 Downing and MI6,” Britain’s foreign spying agency. Subsequently, former MI6 chief John Scarlett joined Dataminr as a “senior advisor.”
A separate leaked memorandum prepared for Denmark’s US embassy brags “no other company has real-time access to the full public Twitter firehose.” As such, Dataminr could provide “indications and warnings of breaking events…and themes relevant to special operations, real-time situational awareness [of] breaking events as they unfold,” and “the ability to explore an individual’s past digital activity on social media and discover an individual’s interconnectivity and interactions with others on social media.”
Such services seem to violate Twitter’s developer agreement, both then and now, which is concerning given the social network is itself a longtime shareholder in Dataminr. In May 2016, public scrutiny of this relationship led to the company being prohibited from offering its services to intelligence agencies, a move harshly condemned by then-CIA director John Brennan. Dataminr provided a means by which to slyly circumvent restrictions on the Agency’s ability to spy on Americans.
In December that year, Twitter cut off US “fusion centers” – highly controversial police spying units – from purchasing Dataminr’s geospatial intelligence data, which allowed for drilling down into activity related to individual tweets, and posts linked to specific events and keywords. Yet, fusion centers continued to be granted access to “tailored breaking news alerts based on public tweets” through a “limited version” of Dataminr. As a company spokesperson effectively confirmed at the time, the announced change meant very little in practice.
The fix is in?
Putting all these facts together, we are left to speculate whether, in the manner of an iceberg, the Politico joint letter was just the visible tip of something far larger, and more destructive, than was apparent at surface-level during the 2020 presidential election campaign.
In June that year, the FBI extended its existing agreement with Dataminr, which was already worth over $1 million. The timing was precipitous, for at the end of the previous month, George Floyd was murdered by police, and the U.S. was instantly and repeatedly engulfed by incendiary large-scale protests, spanning many major cities.
It was later revealed Dataminr kept a close eye on this upheaval every step of the way, tipping off police to the identities of demonstrators, their locations and movements, and developments on-the-ground as they happened. The company moreover monitored all social media mentions of “officers involved in Floyd’s death,” forwarding its findings to multiple clients.
It is likely that a great many innocent people were wrongly tagged as troublemakers in the process. Dataminr’s work tracking down gang members on social media led to any content “that could be tangentially described” as gang-related being “sucked into Dataminr’s platform.” Sources within the company claimed, “all that really mattered…was finding as much danger as possible, real or perceived, and transmitting it to the police.”
The George Floyd protests were just one tumultuous chapter in a highly turbulent year. At the start of 2020, the COVID19 pandemic rocked the world – come the end, Donald Trump was firing up his base by claiming the U.S. establishment intended to rig the forthcoming presidential vote, and he wouldn’t accept the result if he lost.
Heading into election day, every major polling firm consistently recorded that Biden had an extremely comfortable lead over his rival. The NY Post’s Hunter Biden revelations were a “black swan” event with the potential to derail a smooth, indisputable Democratic victory. The US intelligence community – with which Trump had a highly combative relationship before and after entering the Oval Office – would have every reason to ensure those incriminating emails remained dead and buried.
The joint letter provided one mechanism to achieve this end, and Morrell and his cronies eagerly rose to the challenge. Dataminr would’ve provided quite another – and the opportunity to root out and paint a target upon anyone asking awkward questions about Twitter’s proscription of the NY Post, and in turn the 2020 election result.
Given the U.S. national security state’s desperation to rid the country of President Trump at all costs, it would indeed be quite remarkable if the company’s technology wasn’t employed for these purposes.
Feature photo | Illustration by MintPress News
Kit Klarenberg is an investigative journalist and MintPresss News contributor exploring the role of intelligence services in shaping politics and perceptions. His work has previously appeared in The Cradle, Declassified UK, and Grayzone. Follow him on Twitter @KitKlarenberg.
The post Did Intel-Linked Dataminr Play Sinister Role in Hunter Biden Laptop Suppression? appeared first on MintPress News.
